PRODUCTS
Improved productivity and stable production
As Your Single Source for M-E-I-K (Mechanics - Electronics - IT - Knowledge), Okuma offers this CNC to build an advanced “digital twin” that faithfully reproduces machine control and machining operations and creates new value.
In addition, the product helps improve productivity and realize stable production, featuring ease of use that allows customers to use their machining know-how. Additional features are: control technology that achieves high-speed and high-accuracy machining, energy-saving solutions that achieve both high productivity/accuracy and eco-friendliness, and robust security functions to protect against the increasing threat of cyber attacks.
Faithful reproduction of machines and processing — Digital support for shop floor workDigital Twin
"Okuma’s two digital twins" made possible by an office PC and a next-generation CNC reduce machine downtime and improve machine utilization
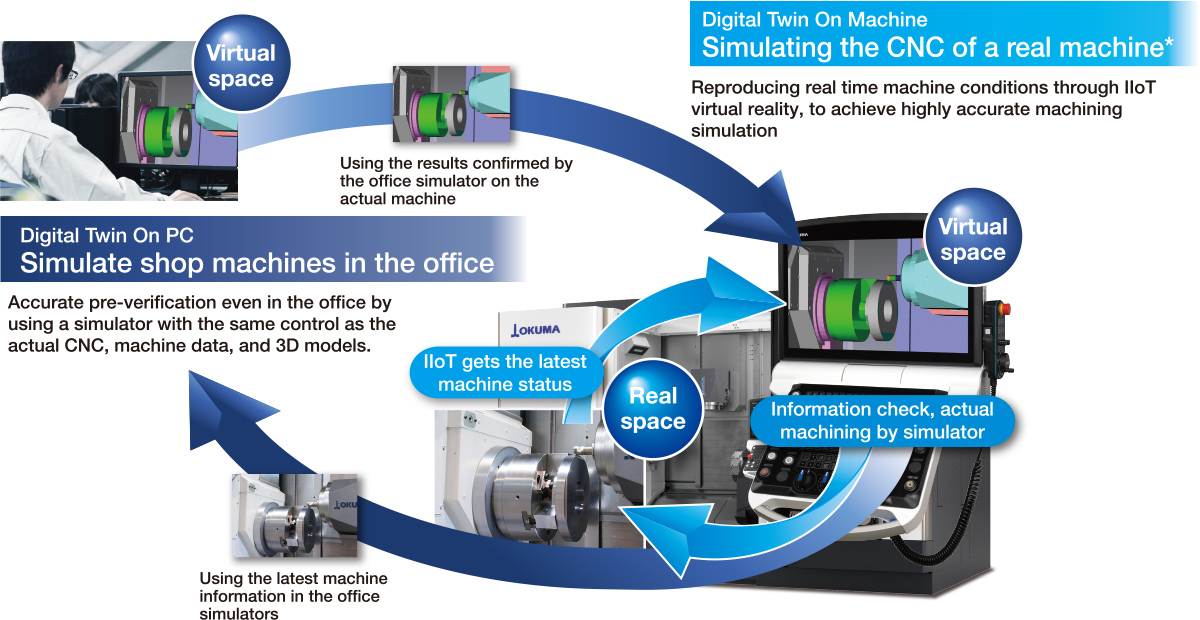
* The simulator is an OSP-P500 option.
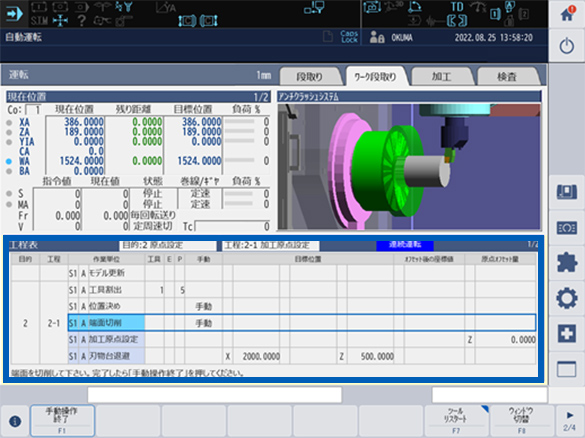
Super easy for novice operators — using skilled machinist shop floor experienceInnovative Operations
Guides and assists operators in a series of parts machining, from preps to cutting and inspection
- It’s also possible to customize the procedure and utilize end-user knowhow.
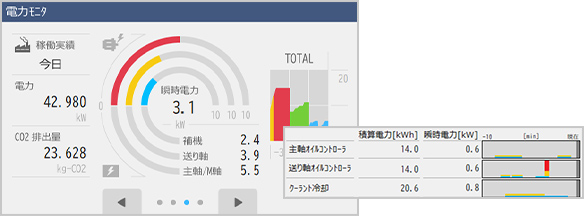
Combining Eco-friendliness with High Productivity and High Accuracy

Equipped with ECO suite plus, Green-Smart Machine contributes to the reduction of carbon dioxide emissions
Next-Generation Energy-Saving System

The ECO suite plus Power Monitor visualizes carbon dioxide emissions in real time
Keeping machines and factories protected and running in a connected world.Cybersecurity
Increasing cyber resilience and protection of the basic performance of machines, part programs, and other assets with robust security functions.
- Defense
-
- Identification and authentication of operators and communications to prevent unauthorized access and connections, etc.
- Protection
-
- Whitelisting of allowed files and applications
- Tamper prevention, anomaly detection, etc. to control damage
- Data restoration
-
- Control software, data backup functions, etc.

